Over-encrypt - Installation Guide
In order to run the client application it is necessary to install a Mozilla Firefox browser (version 3.5 or later), whilst to run the server software it is necessary to install the Java Run Time Environment (version 1.6 or later), an Apache TomCat web server (version 6.0 or later), and a PostgreSQL database server (version 8.3 or later).In the following, we illustrate the installation procedure of the iOverEncrypt software on Windows platforms using the pre-compiled version of the application provided with this prototype.
The following steps specify how to create the relational schemes of the server database (called iOverEncryptDB) and how to initialize the relations with data corresponding to the service provider administrator.
- Uncompress the file Win_iOverEncrypt.zip.
- Open a DOS prompt and type: psql -U postgres .
- In the PostgreSQL shell type: create database "iOverEncryptDB".
- Exit the PostgreSQL shell typing: \q .
- Open a DOS prompt and type: psql -h 127.0.0.1 -U postgres -d "iOverEncryptDB" < $LOCAL\iOverEncryptDB.sql where the variable name $LOCAL refers to the directory into which you have uncompressed the Win_iOverEncrypt.zip archive.
The following steps specify how to install the web application under TomCat web-server.
- Move the folder \srv_iOverEncrypt into the $CATALINA_HOME\webapps directory (the symbolic name $CATALINA_HOME is used to refer to the full pathname of the directory containing the installed release of the TomCat web server).
- Create the text file "ioverenc.conf" into the TomCat main directory ($CATALINA_HOME), where you find also the \webapps subdirectory. The file "ioverenc.conf" must contain the following: serverpath=$CATALINA_HOME\\webapps\\srv_iOverEncrypt\\
The following steps specify how to setup the client application (a Firefox plugin).
- Go to the Firefox drop down menus at the top of the browser. Select File -> Open File then select the iOverEncrypt@… file and click on the Open button.
- Browser’s cookies functionality must be enabled. The first time you use the iOverEncrypt extension, the plug-in will be unable to read the full file pathnames onto the hard drive, due to browser security settings. This is a known issue when using Firefox 3+. To overcome this, follow these steps: (i) enter "about:config" (without quotes) in the address bar of Firefox, and click the confirmation button to change your browser settings; (ii) when the settings page appears, right-click anywhere on the page and select New->Boolean; (iii) enter "signed.applets.codebase_principal_support" (without quotes) as a new preference name; (iv) click OK.
How to Use the Tool
This section describes step by step a simple example showing how to use the tool. The example will show you how to create three accounts and how to use the BEL and SEL functionalities of the outsourcing model. Start the iOverEncrypt extension from the drop down menu of Mozilla Firefox. Tthe login page of the iOverEncrypt will appear.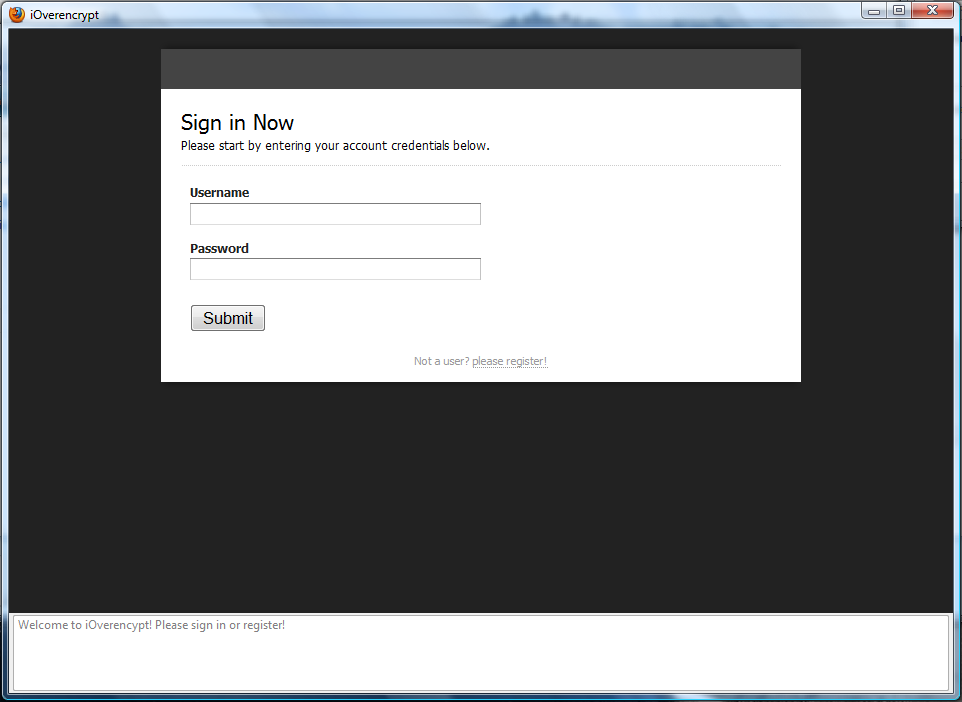
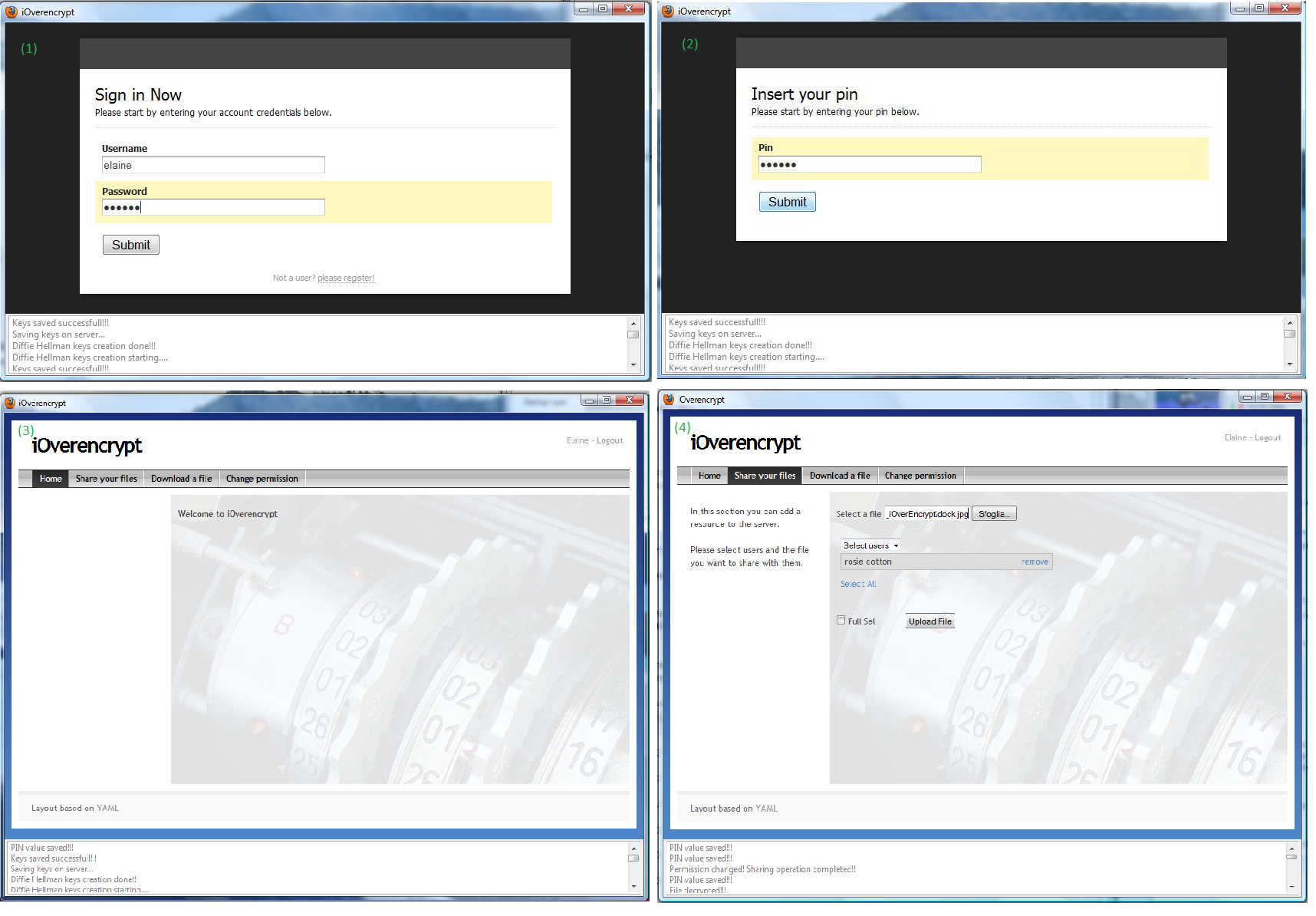
- Register a new account for Elaine Marley with Username:elaine and Password:elaine (see next figure).
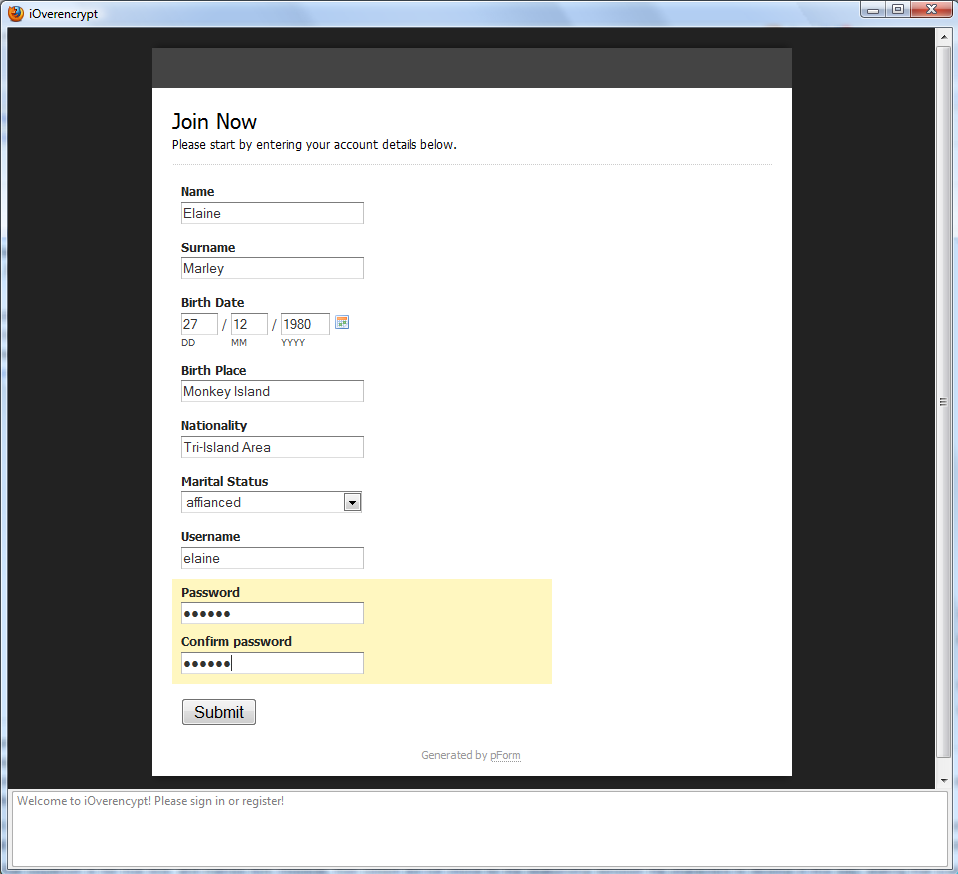
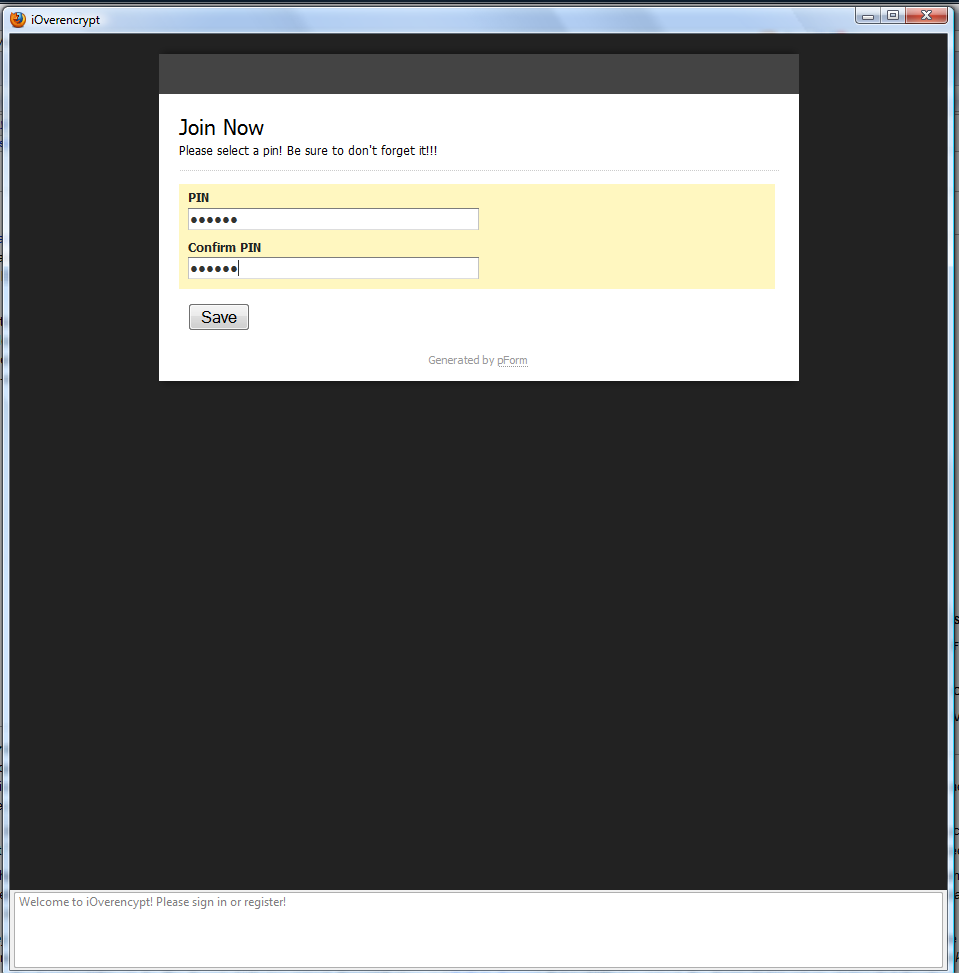
This operation generates a pair of public/private Diffie-Hellman keys. Subsequently, the system will require a PIN composed at least of 5 alphanumerical characters (e.g., elaine). The PIN is used to symmetrically encrypt the copy of the Diffie-Hellman private key bound to the current user. The encrypted private key and the public key are stored at the remote server. When the current user will again log into the system, the client component will download the corresponding Diffie-Hellman keys from the server and will ask for the insertion of the PIN in order to retrieve the plaintext of the Diffie-Hellman secret key. The next picture depicts the PIN insertion window.
- Register a new account for Rosie Cotton with Username:rosie and Password:rosie.
- Register a new account for Arthur Dent with Username:arthur and Password:arthur.
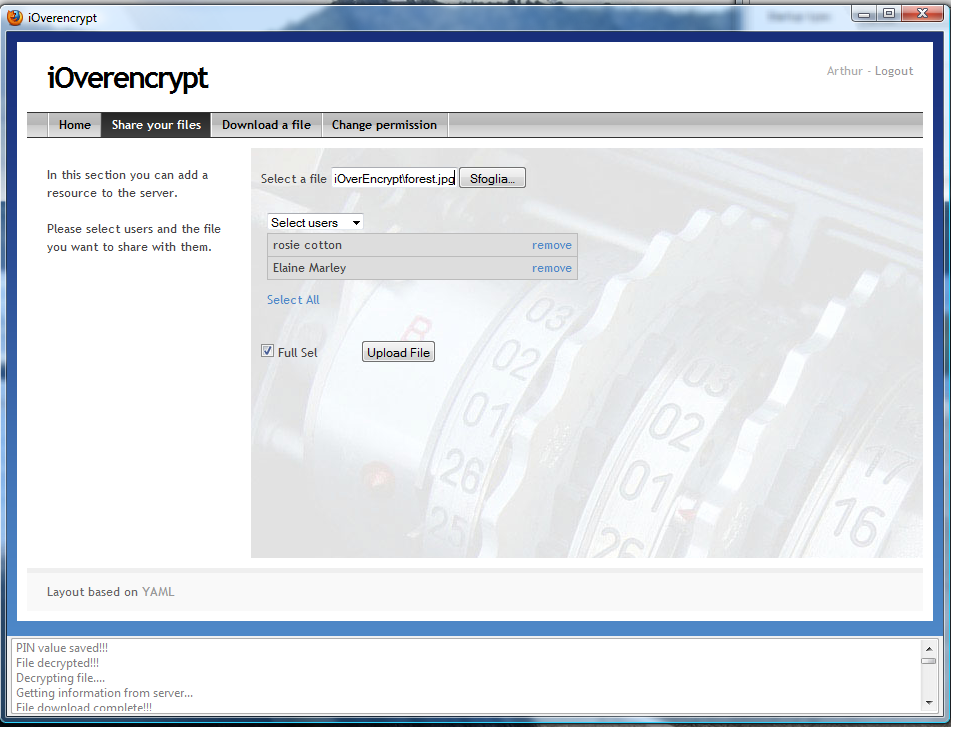
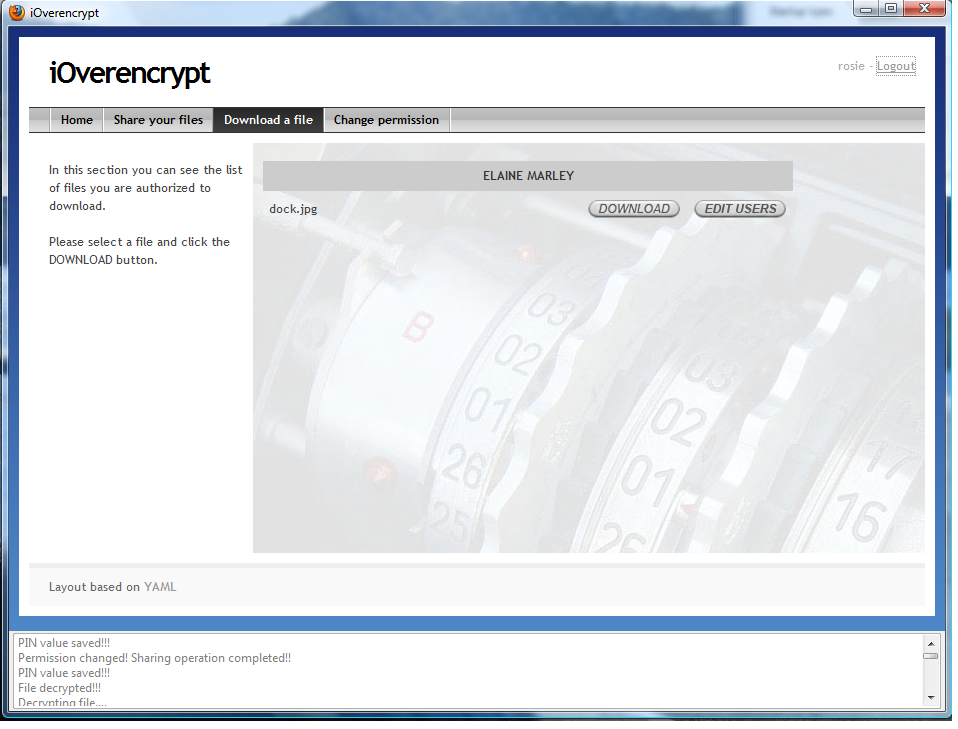
- Sign in as Elaine Marley and, from the menu at the top of the iOverEncrypt window, select the "Share your file" entry. Then, upload a resource, say dock.jpg, to share with the user Rosie Cotton. Finally, log out the iOverEncrypt application clicking the corresponding entry at the top-right part of the window. The next figure depicts the windows of the iOverEncrypt application corresponding to the above steps.
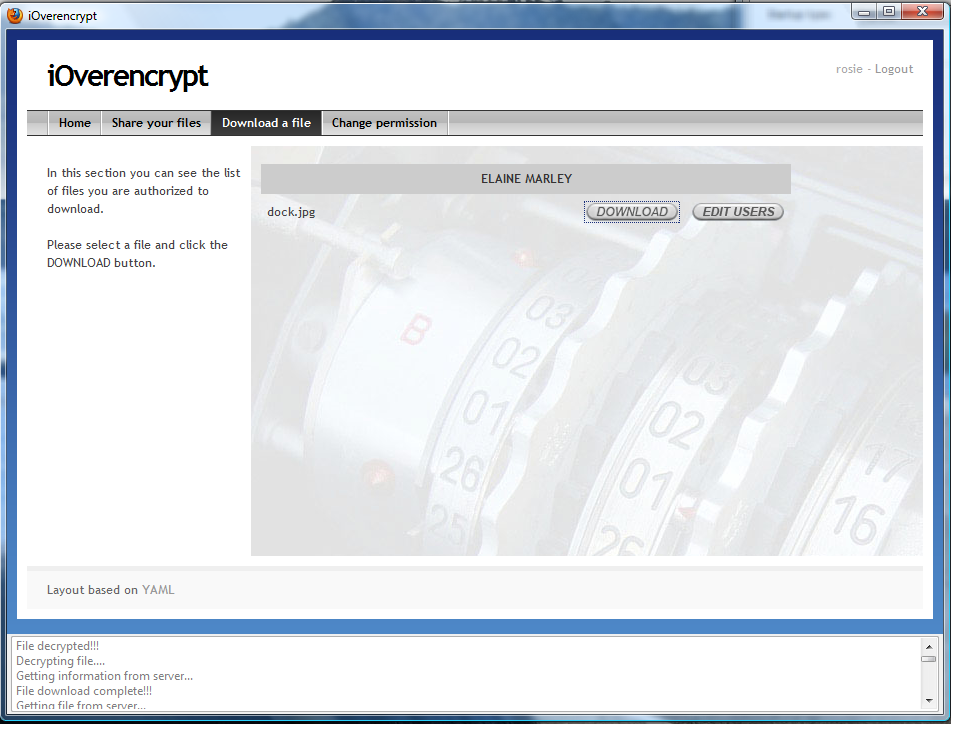
- Sign in as Rosie Cotton, go to the menu and select the "Download a file" entry. Then, choose to download the resource shared from the user Elaine Marley. The next figure illustrates the download page shown by the GUI.
- Sign in as Arthur Dent, go to the menu and select the "Share your file" entry. Then, select Rosie Cotton and Elaine Marley from the users list and select the "Full-Sel" check-box to upload a resource, say forest.jpg. Finally, log out clicking at the top-right of the window (see next picture).
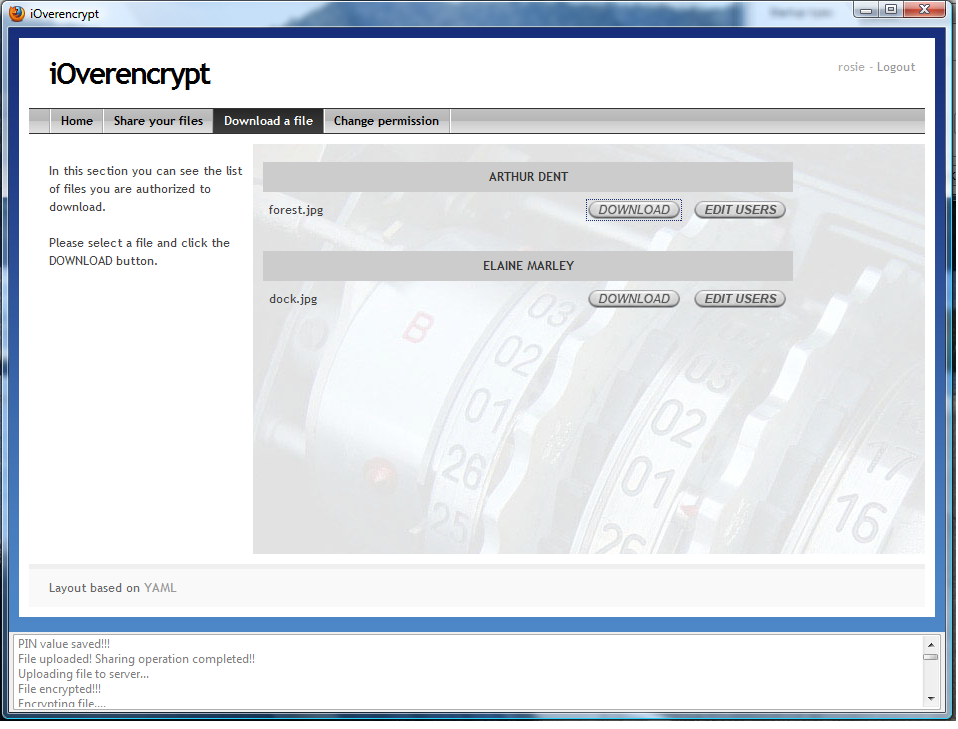
- Sign in as Rosie Cotton, go to the menu and select the "Download a file" entry. Then, choose to download the resource shared from the user Arthur Dent. Then, log out (see next picture).
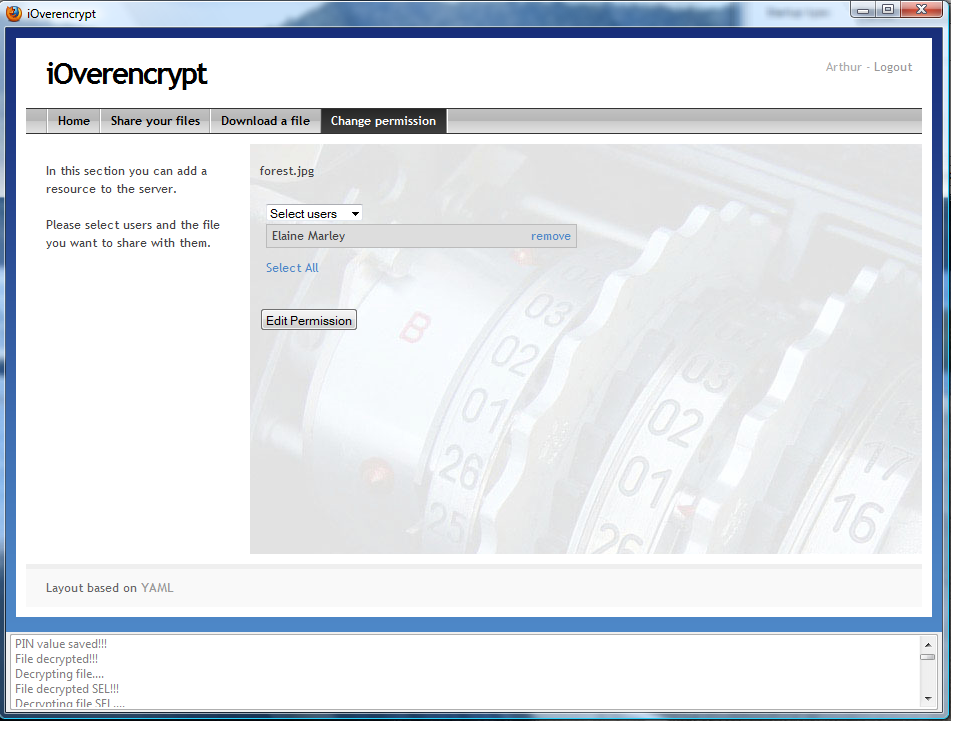
- Sign in as Arthur Dent, go to the drop down menu and select the "Download a file" entry. Then, choose the "Edit Users" button for the resource named forest.jpg. Choose to remove Rosie Cotton from the list of authorized users and click to the "Edit Permission" button. The next figure illustrates the page shown by the GUI to edit the sharing permission decided by a user.
- Sign in as Rosie Cotton, and check the removal of the file forest.jpg from the set of resources she is authorized to access. The next figure shows the download page of Rosie Cotton after her access permissions has been changed by Arthur Dent.